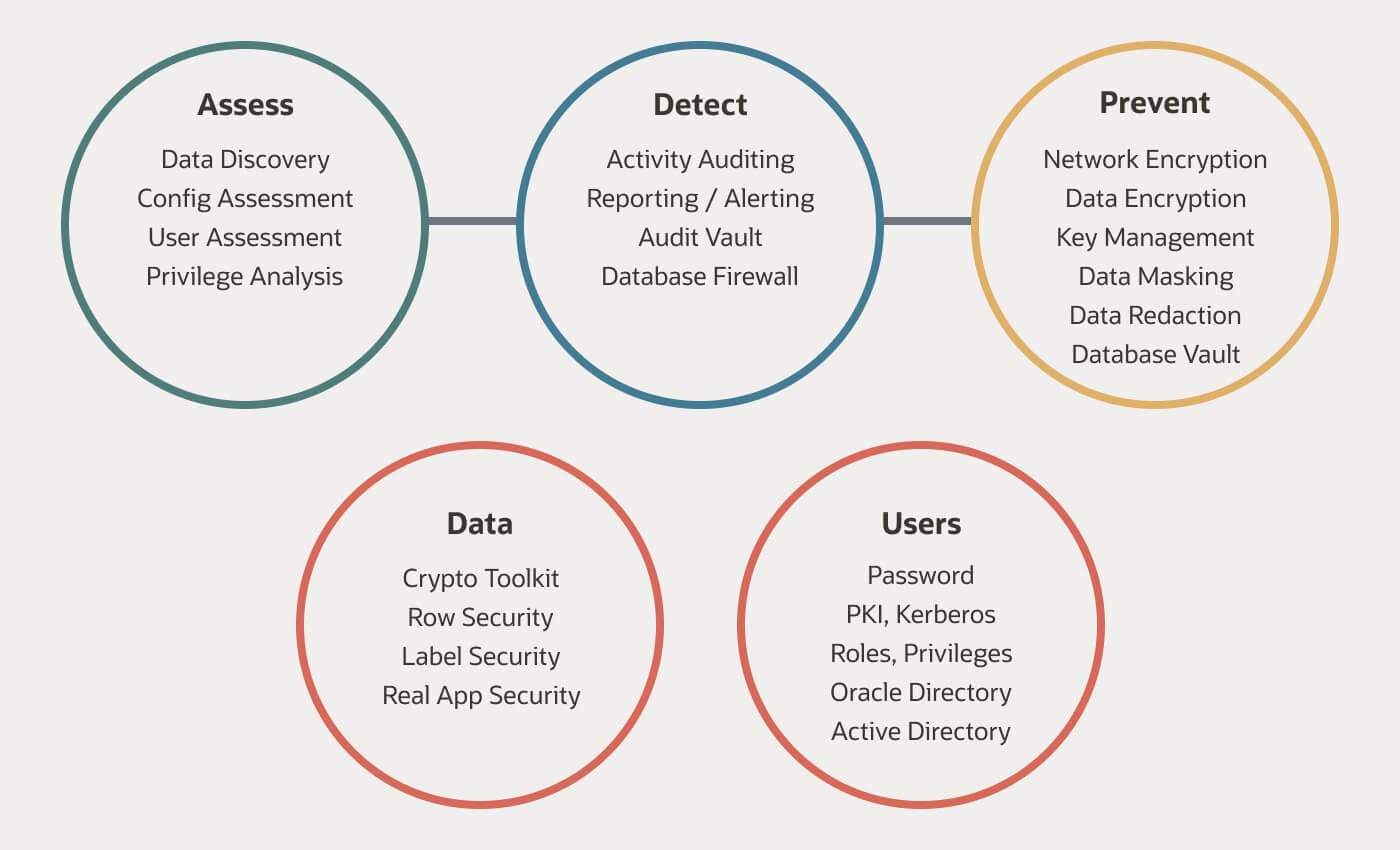
Introduction
In today’s digital age, data security is of utmost importance. With the increasing number of cyber threats and data breaches, it is crucial for businesses and individuals to implement best practices in database management to protect sensitive information. This blog post will explore some essential strategies and techniques to secure your data effectively.
1. Regularly Update and Patch Your Database Software
Keeping your database software up to date is essential for maintaining a secure environment. Vendors regularly release patches and updates to address vulnerabilities and improve security. By promptly applying these updates, you can protect your data from potential exploits.
2. Implement Strong Authentication and Access Controls
Controlling access to your database is vital in preventing unauthorized users from gaining entry. Implement strong authentication mechanisms such as multi-factor authentication and enforce strict password policies. Additionally, assign access privileges based on the principle of least privilege, ensuring that users only have access to the data they need to perform their tasks.
3. Encrypt Your Data
Encrypting your data is an effective way to protect it from unauthorized access. Utilize encryption techniques such as Transparent Data Encryption (TDE) or column-level encryption to safeguard sensitive information. This ensures that even if an attacker gains access to the database, the data remains unreadable without the decryption key.
4. Regularly Backup Your Data
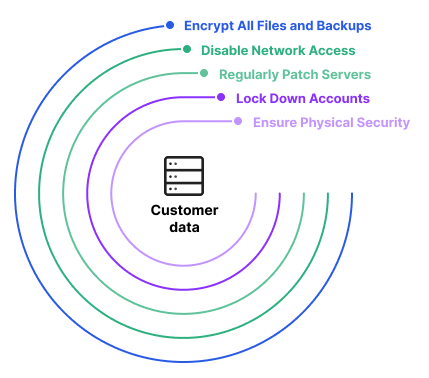
Backing up your data is crucial in case of data loss or a security breach. Implement a robust backup strategy that includes regular backups and offsite storage. Test the restoration process periodically to ensure the integrity of your backups and the ability to recover data when needed.
5. Monitor and Audit Database Activity
Monitoring and auditing database activity allows you to detect any suspicious behavior or unauthorized access attempts. Implement a comprehensive logging mechanism that records all database activities. Regularly review these logs to identify any anomalies and take appropriate action.
6. Implement Database Firewall
A database firewall acts as a barrier between your database and potential threats. It monitors incoming and outgoing traffic, filtering out malicious requests and preventing unauthorized access.
Summary
Securing your data is not just about having a strong password or using encryption. It requires a comprehensive approach that encompasses various aspects of database management. This blog post will cover key best practices such as regular backups, access control, encryption, and monitoring. By following these guidelines, you can significantly reduce the risk of data breaches and ensure the confidentiality, integrity, and his response availability of your valuable data.
- Q: What is database management?
- A: Database management refers to the process of organizing, storing, and securing data in a structured manner to ensure its availability, integrity, and confidentiality.
- Q: Why is securing data important?
- A: Securing data is crucial to protect sensitive information from unauthorized access, prevent data breaches, maintain customer trust, and comply with data protection regulations.
- Q: What are some best practices for securing data in a database?
- A: Some best practices include implementing strong access controls, regularly updating and patching database software, encrypting sensitive data, conducting regular backups, and monitoring database activity.
- Q: How can I ensure strong access controls?
- A: You can ensure strong access controls by implementing role-based access control (RBAC), using strong and unique passwords, regularly reviewing and revoking unnecessary privileges, and limiting physical access to database servers.
- Q: What is data encryption?
- A: Data encryption is the process of converting plain text data into a coded form (cipher text) to prevent unauthorized access. It ensures that even if the data is compromised, it remains unreadable without the decryption key.
- Q: How often should I back up my database?
- A: It is recommended to regularly back up your database, ideally on a daily basis or depending on the frequency of data changes. This helps in quickly recovering data in case of accidental deletion, hardware failure, or other emergencies.
- Q: Why is monitoring database activity important?
- A: Monitoring database activity allows you to detect and respond to any suspicious or unauthorized activities promptly. It helps in identifying potential security threats, unusual patterns, and ensuring compliance with security policies.